NetTunnel
NetTunnel
NetTunnel is a TCP/IP tool that is designed to allow ingress traversal through firewalls where the rules cannot be altered.
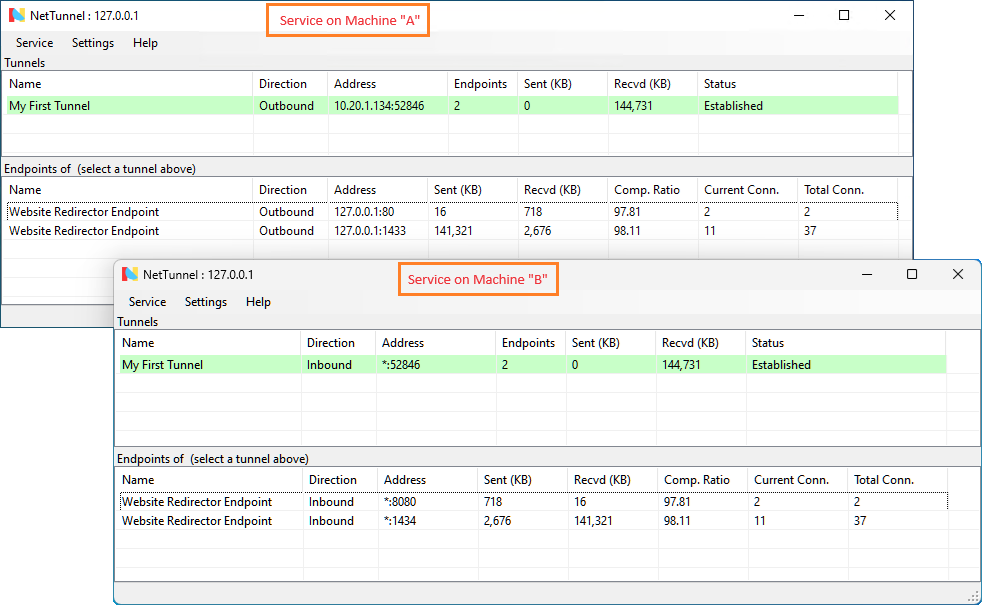
This is accomplished by installing the NetTunnel software at each location where the connection needs to be made FROM and TO. You will then create an OUTBOUND tunnel at the location that is behind a firewall, by doing so the NetTunnel software will reach out to the other remote installation and create an associated INBOUND tunnel. The INBOUND installation would be at a location where you can receive an inbound connection (such as home).
Once configured, the NetTunnel service installation with the OUTBOUND tunnel will make a outgoing connection to the other service.
Once the tunnel is connected you can add/manage endpoints, which are nothing more than a listening port that will pump data through the tunnel, exit at the other NetTunnel service installation and make a connection to the configured endpoint address and port.
Operational concept
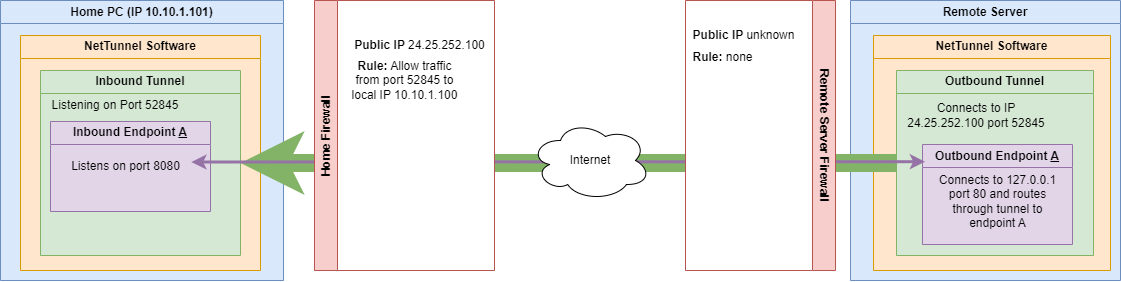
Note that in the diagram above, that we are routing to the remote server, but we do not have its IP address nor do we have any inbound firewall rules defined. All data exchanged between the INBOUND and OUTBOUND endpoints is routed through the encrypted and compressed tunnel to the corresponding endpoint. That tunnel was established as an outbound connection FROM the remote server.
3rd and subsequent endpoint hops
If you are in a situation where both endpoints are behind firewalls, you can get creative and have both endpoint tunnels reach out to a 3rd (or 4th, or 5th....) location which can accept incoming connections from both sites and pipe data between them.
Notes
- All configuration, handshakes and tunneling is completed through a single connection using ReliableMessaging.
- Encryption keys are provided by diffie hellman to create and exchange a 1532bit key for each tunnel at each startup.
- All data exchanged though the tunnel encrypted using the NASCCL symmetric cipher.
- All data exchanged though the tunnel is compressed using the deflate algorithm.
- The UI connects to standard tunnel service provider and inherits all the same encryption and compression benefits.
- All endpoint configuration is stored to the NetTunnel user account so you can configure settings for others and limit their access.
 This is open source software licensed as MIT License. You can obtain the source code from
This is open source software licensed as MIT License. You can obtain the source code from